In the ever-evolving landscape of cybersecurity, protecting an organization’s most critical assets is paramount. Among these, Tier Zero Assets (or Tier 0) stand out as the most sensitive and vital components of an IT infrastructure. These assets, if compromised, can grant attackers complete control over a network, leading to devastating consequences such as data breaches, operational paralysis, and financial losses. This article provides a detailed exploration of what Tier Zero Assets are and offers comprehensive strategies for securing them, drawing from industry best practices and modern security frameworks.
What Are Tier Zero Assets?
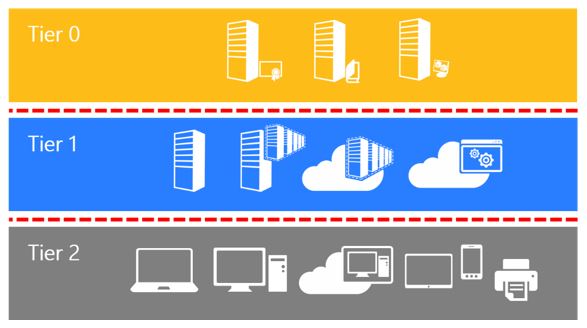
Tier Zero Assets are the most critical systems and identities within an organization’s IT environment. They are defined by their ability to control access to other systems and data, making them the cornerstone of an organization’s security infrastructure. In the context of Active Directory (AD), a widely used identity and access management system, Tier 0 assets include:
- Domain Controllers (DCs): Servers that manage authentication and authorization for an entire domain, storing user credentials, group policies, and other critical information.
- Enterprise Admin Accounts: Accounts with the highest level of privileges across an AD forest, granting full control over all domains and forests.
- Schema Admin Accounts: Accounts that can modify the AD schema, which defines the structure of objects in the directory.
- Domain Admin Accounts: Accounts with administrative privileges over a specific domain.
- Other High-Privilege Systems and Accounts: This includes cloud admin accounts, identity management systems, Microsoft Exchange Server (without split-permissions), Microsoft System Center Configuration Manager (SCCM) if managing Tier 0 assets, and Azure AD Connect (depending on configuration).
The concept of Tier 0 originates from Microsoft’s security models, such as the Enhanced Security Administration Environment (ESAE) (now retired) and the Enterprise Access Model, where these assets are referred to as the “control plane” of the IT environment. According to sources like Dark Reading, Tier 0 assets are those that, if compromised, allow attackers to gain access to any system they desire, underscoring their critical nature.
Importance of Tier Zero Assets
Tier Zero Assets are the epicenter of control for authentication and authorization across an enterprise. Their compromise can lead to:
- Total System Takeover: Attackers can deploy malware, steal sensitive data, or establish persistence within the network.
- Primary Targets for Attackers: Sophisticated attackers use techniques like Kerberoasting and Pass-the-Hash to exploit these assets.
- Regulatory and Financial Risks: Breaches can result in regulatory penalties and significant financial losses.
- Prioritization of Security Efforts: With thousands of potential attack paths in a typical enterprise AD environment, focusing on Tier 0 assets helps organizations address the most dangerous vulnerabilities first.
Securing these assets is not only a technical necessity but also a strategic imperative for compliance with frameworks like the NIST Cybersecurity Framework and ISO 27001.
How to Secure Tier Zero Assets
Securing Tier Zero Assets requires a multi-layered approach that combines traditional security practices with modern, advanced techniques. Below are key strategies, supported by industry insights and tools:
1. Identify and Classify Tier 0 Assets
The first step in securing Tier 0 assets is to identify and classify them accurately. This involves:
- Conducting a thorough inventory of all IT assets.
- Using tools like BloodHound or Tenable Identity Exposure to map Tier 0 assets and identify potential attack paths.
- Referencing resources like SpecterOps’ TierZeroTable to determine which AD and Azure assets qualify as Tier 0.
2. Implement the Principle of Least Privilege
To minimize the risk of unauthorized access:
- Grant only the necessary privileges to users and systems.
- Use Role-Based Access Control (RBAC) to restrict access to Tier 0 assets.
- Avoid using domain admin accounts for routine tasks to reduce exposure.
3. Segregate Administrative Duties
Implementing a tiered administration model creates buffer zones to prevent privilege escalation:
- Tier 0 Administrators: Manage domain controllers and other critical systems.
- Tier 1 Administrators: Handle user accounts and less critical systems.
- Tier 2 Administrators: Manage end-user devices and applications.
- In specific cases, deploy a separate AD forest for isolation.
4. Use Privileged Access Management (PAM) Solutions
PAM solutions enhance security by:
- Managing, monitoring, and securing privileged accounts.
- Enforcing policies like session recording, approval workflows, and time-limited access.
- Examples include One Identity Safeguard and CyberArk.
5. Harden Tier 0 Systems
To protect Tier 0 systems:
- Apply security baselines and harden domain controllers.
- Regularly update and patch systems to address known vulnerabilities.
- Deploy anti-malware, firewalls, and Endpoint Detection & Response (EDR) tools.
6. Implement Network Segmentation
To limit lateral movement:
- Isolate Tier 0 assets on a separate network segment.
- Use firewalls and access control lists (ACLs) to restrict traffic to and from Tier 0 assets.
7. Monitor and Audit Access
Continuous monitoring is critical:
- Implement logging for all access to Tier 0 assets.
- Use Security Information and Event Management (SIEM) systems to detect and alert on suspicious activities.
- Regularly review audit logs for anomalies.
8. Modern Protection Methods
Modern security practices provide robust protection:
- Authentication Policies: Use Kerberos Authentication Policies (based on FAST/Kerberos Armoring) to restrict Tier 0 account usage to specific hosts, preventing credential theft. This requires a domain functional level of Windows Server 2012 R2 or higher.
- Privileged Access Workstations (PAWs): Use dedicated, domain-joined, or Intune-managed workstations for Tier 0 admin logons, such as those using Azure Virtual Desktop.
- Cloud-Based Security: Leverage Azure Entra ID features, including:
- Multi-Factor Authentication (MFA): Adds an extra layer of security.
- Conditional Access: Restricts access based on conditions like device compliance.
- Identity Protection: Detects and mitigates identity-based threats.
9. Automation and Tools
Automation streamlines security management:
- Use PowerShell tools for managing Tier 0 assets.
- Tools like BloodHound help visualize and manage attack paths within AD.
10. Additional Security Measures
- Add privileged users to the Protected Users security group to enhance credential protection.
- Enable “Require rolling NTLM secret for NTLM authentication” for users requiring smart card logon.
- Maintain Breakglass Accounts for emergency access, ensuring they are tightly controlled.
- Follow the Clean Source Principle to ensure Tier 0 systems are free from malware and unauthorized changes.
- Review and clean ACLs at the domain root level, considering breaking inheritance on Tier 0 Organizational Units (OUs).
Implementation Steps for a Tiered Administration Model
| Step | Action |
|---|---|
| 1. Identify Tier 0 Resources | Use tools to map and classify Tier 0 assets. |
| 2. Create New Administrative Accounts | Restrict Tier 0 accounts from accessing lower-tier systems. |
| 3. Configure Authentication Policies | Set up Kerberos policies to limit Tier 0 account usage. |
| 4. Deploy PAWs | Use dedicated workstations for Tier 0 admin logons. |
| 5. Monitor and Update | Continuously update policies and monitor for breaches. |
Best Practices
- Regular Security Assessments: Conduct vulnerability assessments and penetration testing to identify weaknesses.
- Employee Training: Educate administrators on the importance of Tier 0 assets and secure practices.
- Backup and Recovery: Regularly back up Tier 0 assets and test recovery processes.
- Compliance and Audit Readiness: Align with frameworks like NIST CSF and ISO 27001.
Conclusion
Tier Zero Assets are the linchpin of an organization’s IT security, controlling access and authentication across the enterprise. Their compromise can lead to catastrophic breaches, making their protection a top priority. By identifying these assets, implementing strict access controls, leveraging modern security tools, and fostering a culture of security awareness, organizations can significantly reduce the risk of a breach. The strategies outlined in this article, supported by industry-leading resources, provide a roadmap for securing Tier Zero Assets and ensuring the resilience of the IT infrastructure.







